
This post is a part of Tor v3 tutorial. Other parts are:
- Hidden Service setup
- PKI and TLS
- Client Authentication
- Installing client certificates to Firefox for Android
As we now have working Public Key Infrastructure, we are ready to use it for more than encrypting traffic (which is already encrypted by Tor). We can very easily turn on client verification on our server. This will prevent anybody not having valid certificate issued by us from visiting our hidden webpage – just in case hiding domain name in hidden services version 3 leaks the name somehow (which should not happen anymore in v3). In this part we will issue client certificate (the procedure is almost identical to server certificate), then configure httpd to require client identification and finally configure Firefox to try sending the certificate. Let’s go!
Issuing user certificate
In my case tmp directory emulated client machine and ca is my Cerificate Authority, which issues certificates. We start by creating request on client side, then sign it on CA side.
$ mkdir tmp $ cd tmp $ openssl genrsa -out v3l0c1r4pt0r@gmail.com.key.pem 4096 Generating RSA private key, 4096 bit long modulus ........++ ..............................................++ e is 65537 (0x010001) $ openssl req -config ../ca/intermediate/openssl.cnf -key v3l0c1r4pt0r@gmail.com.key.pem -new -sha256 -out v3l0c1r4pt0r@gmail.com.csr.pem You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [GB]:PL State or Province Name [England]:lodzkie Locality Name []: Organization Name [Alice Ltd]:r4pt0r Test Systems Organizational Unit Name []: Common Name []:v3l0c1r4pt0r@gmail.com Email Address []:v3l0c1r4pt0r@gmail.com $ chmod 400 v3l0c1r4pt0r@gmail.com.*.pem $ cp v3l0c1r4pt0r@gmail.com.csr.pem ../ca/intermediate/csr/ $ cd ../ca $ openssl ca -config intermediate/openssl.cnf -extensions usr_cert -days 375 \ > -notext -md sha256 -in intermediate/csr/v3l0c1r4pt0r@gmail.com.csr.pem \ > -out intermediate/certs/v3l0c1r4pt0r@gmail.com.cert.pem Using configuration from intermediate/openssl.cnf Enter pass phrase for /home/r4pt0r/Research/cubie/newtor/ca/intermediate/private/intermediate.key.pem: Check that the request matches the signature Signature ok Certificate Details: Serial Number: 4097 (0x1001) Validity Not Before: Feb 27 17:14:40 2018 GMT Not After : Mar 9 17:14:40 2019 GMT Subject: countryName = PL stateOrProvinceName = lodzkie organizationName = r4pt0r Test Systems commonName = v3l0c1r4pt0r@gmail.com emailAddress = v3l0c1r4pt0r@gmail.com X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Cert Type: SSL Client, S/MIME Netscape Comment: OpenSSL Generated Client Certificate X509v3 Subject Key Identifier: ED:24:E6:FF:1D:9B:61:AC:29:66:39:59:FB:5D:77:25:F7:A3:55:47 X509v3 Authority Key Identifier: keyid:3D:AC:8E:21:79:5A:AD:7B:7C:92:92:65:B7:19:D0:E8:00:0E:50:70 X509v3 Key Usage: critical Digital Signature, Non Repudiation, Key Encipherment X509v3 Extended Key Usage: TLS Web Client Authentication, E-mail Protection Certificate is to be certified until Mar 9 17:14:40 2019 GMT (375 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated $ cd ../tmp $ cp ../ca/intermediate/certs/v3l0c1r4pt0r@gmail.com.cert.pem ./ $ openssl pkcs12 -export -inkey v3l0c1r4pt0r@gmail.com.key.pem -in v3l0c1r4pt0r@gmail.com.cert.pem -out v3l0c1r4pt0r@gmail.com.p12 Enter Export Password: Verifying - Enter Export Password:
Last step was packaging certificate and key into PKCS#12 container. That is for securing key (we can encrypt it with password), and is a form required by Firefox. After creation of .p12 (and verifying it is fine), we can (and SHOULD) delete source files, as they are not protected in any way.
Configuring httpd to require user certificate
To enforce client verification, following lines must be added to virtual host configuration, in our case it might go just after SSL certificate file paths.
SSLVerifyClient require SSLVerifyDepth 2
We have to reload httpd for changes to take effect.
Installing certificate to Firefox
At last, to start using newly generated certificate, we should install it to Firefox. The procedure is similar to the one with CA certificate. We need to open Certificate Manager window. Then, instead of going to Authorities, we go to Your Certificates. Then we click on Import and select .p12 file.
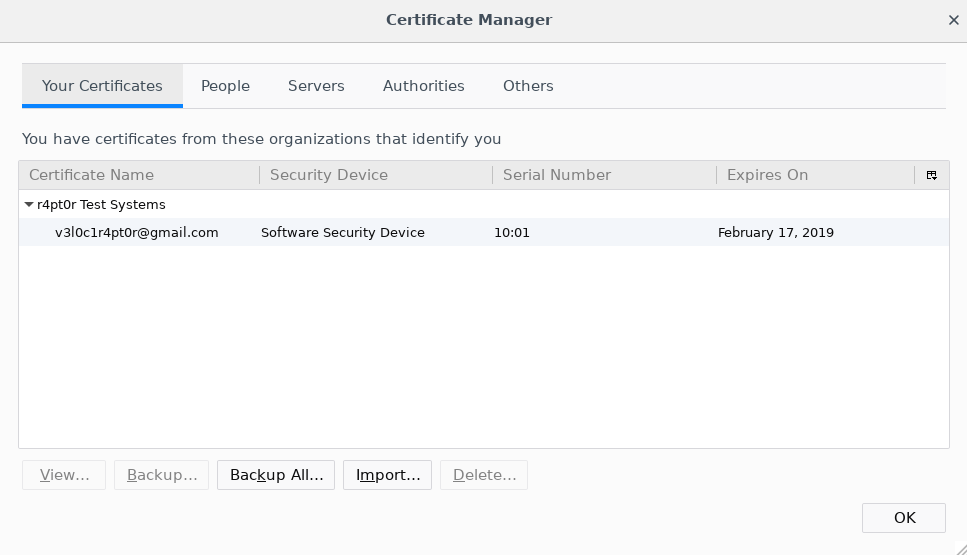
If the file has password, Firefox will ask for it and after successfully reading the content. If everything went well, you should see your certificate on the list. Now we can try connecting to our hidden service. We should see the window like this:
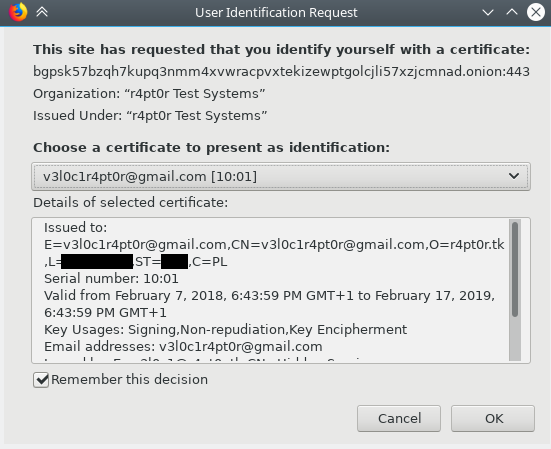
Finally, after confirmation, you should see your hidden service content. Congrats!
